Which of the Following Are Listed Insider Threat Categories
Turncloaks A turncloak is an insider who is maliciously stealing data. The following sections cover the basics of these types of access attacks.
Cert Definition Of Insider Threat Updated
Negligent insiders This may include careless executives or employees with access to privileged information.

. D Latest CS0-002 Dumps Valid Version with 220 QAs LatestContinue reading. To accomplish this kind of attack a hacker can use many tools including the following. The key here is that there are two distinct types of Insider Threats.
INSIDER THREAT SOLUTION ECOSYSTEM Insider threat is a complex problemand there will never be a single one-size-fits-all solution. According to Gartner there are essentially four different types of insider threats. A security engineer is reviewing security products that identify malicious actions by users as part of a companys insider threat program.
Records Checks Purpose Insider Threat Programs use techniques like workforce awareness campaigns and user activity monitoring to prevent deter detect and mitigate future potential insider threats. With each of its types there are several technical and traditional controls that you can take to bolster identification and prevention. The two main types of insider threats are turncloaks and pawns which are malicious insiders and unwilling participants respectively.
Department of Justice DOJ Insider Threat Prevention and Detection. Insider threats vary significantly in intent access level awareness and motivation hence they are not all alike. Organizations of all types and sizes are vulnerable to insider threatsfrom family-owned small businesses to Fortune.
Cause harm and destruction to further their cause. As the name suggests. Select all that apply.
This Order establishes policy and assigns responsibilities for a. An insider threat is a type of cyberattack originating from an individual who works for an organization or has authorized access to its networks or systems. Simple negligence is the most common form of insider threat and also the single most expensive category of employee risk.
Organizations use to determine insider threat risk. Sabotage an insider will use their legitimate access to the network to destroy or damage the company systems or data. Which of the following is the MOST appropriate product category for this purposeA.
For the following Threat Categories 1 Explain the threat 2which type of Control should be put in place for mitigation 3classify the controls as Process Administrative Product or Physical 4State the type of controls whether it will Prevent Detect Correct or Compensate. PRIs generally belong to the categories listed here. These insiders dont have any motivation money or otherwise.
However while several categories of tools have emerged to address insider threat its important to understand exactly what kind of protection they offerand at what cost. -Considerable change in financial circumstances -addictive behaviors -substance abuse. Select all that apply.
More than 35 types of insider threats were reviewed. -Threat can include unathorized disclosure of national security information or through the loss or degradation of department resources or capabilities-Threat can include damage through espionage or terrorism-Any person with authorized access to DoD resources by virtue of employment volunteer activities or contractual relationship with DoD. Cyber terrorists can target businesses state machinery and critical services that would cause the most harm disruption and destruction.
1 2 FEB 2014. They are simply careless in their actions or may have fallen victim to a scam. Although a variety of terms are used constructively by individual government agencies and companies INSAs.
Insider Threat Mitigation Program. This is called an unauthorized access attack. These threat actors are usually focused on disrupting critical services and causing harm.
14 Technology Sample Vendor Used. Which of the following are re portable behavioral indicators. These are employees who engage in inappropriate behavior much of which can fall into the category of Shadow IT.
UEBA View Answer Answer. -Increase risk of information loss -Allow insiders to access more data. Categories of Insider Threats broadly classifies the nature of insider threats organizations face today with common terms that facilitate information-sharing and learning.
2020 Cost of Insider Threats Global Report. Insider threat types can be classified as follows. In its recent annual report Verizon identified five broad types of insider threats that can affect an organization.
Fraud an insider will steal modify or destroy data for the purpose of deception. Access attributes Professional lifecycle and performance Foreign considerations Security compliance and incidents Technical activity Criminal violent or abusive conduct Financial considerations. Average jury award.
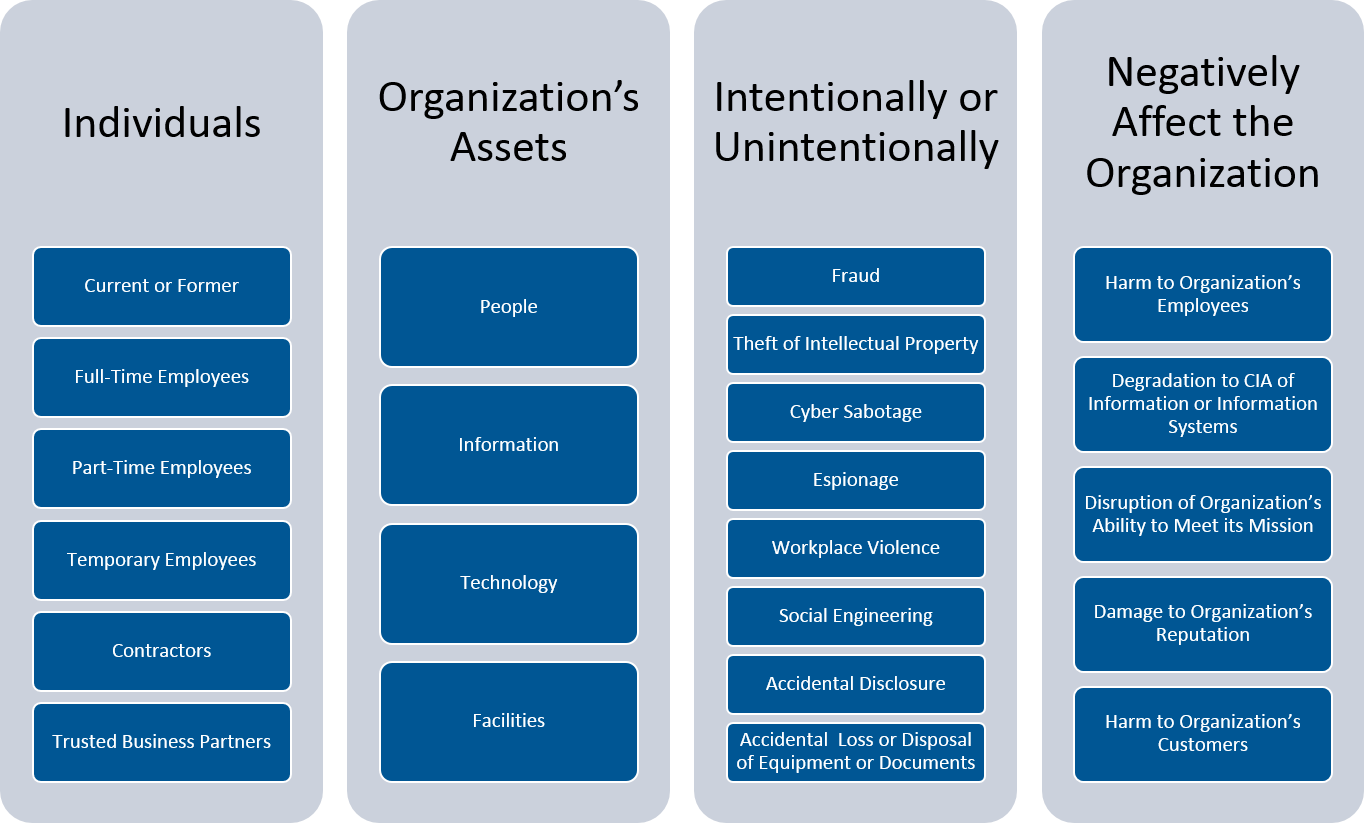
In the most basic form of an access attack a hacker tries to gain illegal access to equipment in your network. An insider threat could be a current or former employee consultant board member or business partner and could be intentional unintentional or malicious. Here are the main types of insider threats.
Identify the types of information and records to locate when performing an insider threat records check. Insider threats who fit this category might. Insider Threats stem from people whether employees former employees contractors business partners or vendors with legitimate access to an organizations networks and systems who exfiltrate data for personal gain or accidentally leak sensitive information.

Insider Threat Definition Types Countermeasures Ekran System

What Is An Insider Threat Examples Of Threats And Defenses

Insider Threat Definition Types Countermeasures Ekran System

Comments
Post a Comment